ISE15/20-21
| Subject: | manpower, cyber security, cyber security talent |

- Information and communications technologies have evolved over the last two decades and become increasingly embedded in virtually every aspect of modern life. Nowadays, people conduct more of their work/lives online and almost every business relies on some forms of digital communications to engage customers. While this trend opens up innovative technologies and e-services such as Internet of Things1Legend symbol denoting Internet of Things ("IoT") is a technology which enables the provision of communications platforms and services for interconnected devices to generate, exchange and consume data with minimal human intervention. With the proliferation of IoT, consumers are bringing more and more Internet connected devices into their homes. These include smart televisions, smart security locks, and smart home hubs that control home lighting, heating and cooling., artificial intelligence2Legend symbol denoting In recent years, artificial intelligence ("AI") has developed not only as a field of research, but also as a technology that expands across a wide range of applications. Some of the most interesting AI applications are outside of computer science in sectors such as transport, healthcare, financial services and marketing. and cloud computing3Legend symbol denoting Cloud computing is the delivery of computing resources (hardware and software) by a party (the service provider) over the Internet to a user (consumer). This delivery or provision is described as a "service" because the user merely uses the computing resources rather than actually acquiring them. See InfoCloud (2020)., this brings new dependencies.
- In an increasingly digitally connected world, government, businesses and society now rely on the integrity of cyberspace and the infrastructure, systems and data which underpin it. This is particularly so in view of ever-increasing amount of sensitive information collected and stored on computers and other devices, for which unauthorized access or misuse could have negative consequences4Legend symbol denoting Dealing with a mega breach (involving more than one million records) costs US$42 million (HK$326 million) on average in 2019. See Allianz Global Corporate & Specialty (2020).. The recent push to work from home during the coronavirus pandemic adds to the concerns over cyber security risks5Legend symbol denoting The shift to work from home brings additional cyber security challenges as employees log on through their home networks or with personal devices that might not be as secure as office environments..
- Indeed, awareness of cyber threats has grown rapidly in recent years, with cyber security incidents6Legend symbol denoting Cyber security incidents include computer virus attack, ransomware, denial of service attack, hacking, theft of information, online fraud, web defacement and leakage of information. being ranked as the most important business risk globally according to a survey conducted in 20197Legend symbol denoting The 2019 survey identifies the top corporate risks for the next 12 months and beyond in 102 countries and territories. See Allianz Global Corporate & Specialty (2020).. There is consequently an increasing need for well-trained cyber security professionals8Legend symbol denoting Cyber security refers to the protection of Internet connected systems (including hardware, software and associated infrastructure), the data on them, and the services they provide, from unauthorized access, harm or misuse. This includes harm caused intentionally by the operator of the system, or accidentally, as a result of failing to follow security procedures. See GOV.UK (2016)., who could analyze, manage and respond to the risks and threats in cyberspace.
- The availability of sufficient technology talent poses a significant cyber security challenge for Hong Kong. Of the 95 780 information technology ("IT") employees in 2018, only 1.2% specialized in IT security. Indeed, Hong Kong is part of the global trend as the shortage of cyber security professionals worldwide is estimated at 3.1 million in 20209Legend symbol denoting See (ISC)2 (2020a).. Among the developed economies, the United Kingdom ("UK") has been among the most proactive in addressing its workforce gap10Legend symbol denoting As estimated by (ISC)2, there is a shortage of 27 408 cyber security professionals in the UK in 2020. with measures on various fronts to assist those already working in or aspiring to work in cyber security profession.
- This issue of Essentials begins with the discussion of manpower development of cyber security professionals in Hong Kong. This is followed by the study of the UK's multi-pronged approach to creating the environment for, and accelerating the development of, the cyber security profession in the country.
Cyber security manpower development in Hong Kong
- Hong Kong is increasingly reliant on the Internet, telecommunications infrastructure and smart devices for daily life, business operation and economic development. For example, some 2.5 million households had access to the Internet at home in 2019, constituting 94.1% of all households. The proportion of business establishments using the Internet was also at a high of 90.3% in 2019.11Legend symbol denoting Most recently, Hong Kong entered into a new era of smart banking, with the Hong Kong Monetary Authority issuing eight virtual banking licences in 2019 to open the door for the financial technology companies to enter the banking industry.
- With Hong Kong becoming more and more digital, the prevalence of cyber security issues is increasingly commensurate. The number of cyber security incidents surged from 4 928 cases in 2015 to 9 458 in 201912Legend symbol denoting See Hong Kong Computer Emergency Response Team Coordination Centre (2020).. Among the establishments using computers/smartphones/the Internet in 2019, about one in every 10 had experienced cyber security incidents over the past 12 months13Legend symbol denoting See Census and Statistics Department (2020a)..
- Cybercrime has also been on the rise in recent years. The Hong Kong Police Force recorded an increase in computer crime cases from 6 862 in 2015 to 8 322 in 201914Legend symbol denoting See InfoSec (2020).. The cases were not just growing in volume but also in their severity. The financial loss due to computer related crime increased from HK$1.8 billion (HK$267,000 per case) in 2015 to HK$2.9 billion (HK$349,000 per case) in 2019.
- With the continuous increase in cyber threats, there were a mere 1 118 or 1.2% of IT employees specializing in IT security in 2018. The majority of these specialists were employed by the IT products and services suppliers (48% of the total) and the financing and business-related sectors (36%)15Legend symbol denoting See Vocational Training Council (2018).. With limited manpower supply, the availability of sufficient technology talent poses a significant cyber security challenge for Hong Kong.
- Nurturing home-grown talent starts with education. Computing curriculum can help students acquire fundamental digital skills and stimulate their curiosity and interests in pursuing further digital studies. Yet, the proportion of the candidates taking ICT in the Hong Kong Diploma of Secondary Education Examination stood at 10.6% in 2019. It was much lower than school provision rate (88.2%) and the enrollment rates for subjects such as Chinese History (11.4%), Accounting (13.6%) and Geography (16.0%).
- As to formal education programme to develop future cyber security talent, studying for a university degree is a traditional route of entry into professional life. Currently, undergraduate degrees in cyber security-related fields include (a) generalist computer science and other STEM-related disciplines that offer cyber security as a core or optional module; and (b) specialism in cyber security (i.e. bachelor's degree in cyber security). The latter provides a direct route to cyber security career, as it teaches students to identify, evaluate and defend against cyber threats and attacks on networks, data and information systems. Students also acquire the skills to design and implement protection and prevention measures16Legend symbol denoting Some bachelor's degrees in cyber security offer concentration options in areas such as cyber security analysis, digital forensics, system security and cloud computing.. Yet, few local universities currently provide degree courses purely in cyber security. Only the Hong Kong Polytechnic University is offering the Bachelor of Science in Information Security, and the Open University of Hong Kong the Bachelor of Science in Cyber and Computer Security.
- Meanwhile, cyber security is a broad and varied profession that those working in it are found across multiple disciplines with a wide range of different competencies. The understanding of what constitutes a cyber security professional may vary. Hence, it is essential to establish an agreed framework of cyber security professionals through qualifications and certifications, whereby cyber security professionals are informed about the different types of cyber security roles available and the career pathways that they need to take to get there17Legend symbol denoting The Hong Kong Monetary Authority, the Hong Kong Institute of Bankers and the Hong Kong Applied Science and Technology Research Institute jointly developed a three-level certification scheme, namely the Certified Cyber Attack Simulation Professional ("CCASP") in 2016. CCASP provides a recognized career path from an entry-level into the industry as a practitioner (Practitioner Level) through to an information security tester (Registered Level), and then to information security specialist (Certified Level). Between December 2016 and November 2020, a total of 68 persons passed CCASP examination at various levels.. Employers can also make use of the agreed framework to easily assess the capabilities of individuals they are employing to perform cyber security roles.
Cyber security manpower development in the United Kingdom
- The UK was ranked first in the latest 2018 Global Cybersecurity Index which measures a country's level of engagement in cyber security.18Legend symbol denoting Hong Kong was not included in the 2018 Global Cybersecurity Index. The index, compiled by the International Telecommunications Union ("ITU"), is assessed along five pillars - capacity building, legal, technical, organizational and co-operation on a country level. For "capacity building", it is calculated based on a country's educational programmes or academic curricula, framework for certification and accreditation of cyber security professional, professional training courses in cyber security, etc.
- Reflecting its strength in "capacity building", the UK employed some 43 000 Full Time Equivalents in a cyber security related role in 2019. More importantly, it has some of the best cyber security professionals in the world. In 2020, 7 590 cyber security professionals in the UK held the Certified Information Systems Security Professional ("CISSP"), the second largest population in the world after the United States. The CISSP certification is one of the most prominent IT security professional certifications which identifies individuals with high standards of competency19Legend symbol denoting To qualify for the CISSP certification, one must pass the examination and has at least five years of cumulative, paid work experience in two or more of the eight domains of cyber security. The eight domains are: (a) Security and Risk Management; (b) Asset Security; (c) Security Architecture and Engineering; (d) Communication and Network Security; (e) Identity and Access Management; (f) Security Assessment and Testing; (g) Security Operations; and (h) Software Development Security..
- Being ranked by ITU as the country most committed to cyber security, the UK has set out in its National Cyber Security Strategy20Legend symbol denoting In November 2011, the UK published the UK Cyber Security Strategy 2011-2016 aiming at, among other things, making the country one of the most secure places in the world to do business online and tackling cybercrime. This national strategy was reviewed and renewed with the publication of the National Cyber Security Strategy 2016-2021 in 2016. The five-year strategy seeks to provide a secure and resilient environment in the UK against cyber threats, as well as supporting the country to be prosperous and confident in the digital world by 2021., which is the government's plan to make the country more secure and resilient in cyber space through three main pillars of "Develop", "Defend" and "Deter". Specifically, the "Develop" pillar aims to develop a self-sustaining pipeline of home-grown talent that will provide the skills to meet the national needs across the public and private sectors21Legend symbol denoting For the other two main pillars, Defend is to protect the UK against evolving cyber threats, respond effectively to incidents, and ensure UK networks, data and systems are protected and resilient; and Deter is to detect and disrupt hostile action against the UK in cyberspace, followed by pursuing and prosecuting offenders..
- Following the National Cyber Security Strategy, the Department for Digital, Culture, Media & Sport22Legend symbol denoting The Department is responsible for delivering the government's policy covering arts and culture, communications and media, sport, tourism, building a shared society and digital connectivity. has, in collaboration with the National Cyber Security Centre23Legend symbol denoting As part of the National Cyber Security Strategy, the National Cyber Security Centre was created in 2016 under the Government Communications Headquarters. It is the UK's lead technical authority on cyber security, helping to make the UK the safest place to live and to do business online. ("NCSC"), implemented a national scheme, CyberFirst, to help develop the cyber security talent pipeline in the UK. CyberFirst contains a wide range of government's initiatives and interventions, which are not only focused on (a) formal educational activities to develop future cyber security professionals; and (b) qualifications and certifications to create clearer career pathways and bring greater coherence to the skills landscape. They also include a wide range of extra-curricular activities to identify talent and develop interests at a young age; and a retraining fund to upskill the current workforce as cyber security professionals.
Formal educational activities
- Formal education provides the universal building blocks that equip young people in pursuing careers in cyber security. In the UK, the CyberFirst Schools initiative certifies those secondary schools which are committed to developing young people's cyber skills. Being certified as a CyberFirst School will be recognized and promoted by NCSC (Figure 1). There are also STEM Ambassadors who are doing outreach work into schools to encourage STEM studies, which can be an excellent starting point for those students aspiring to get into cyber security profession.
- As mentioned above, studying for a university degree is a traditional route of entry into professional life. NCSC delivers the CyberFirst Bursary scheme and CyberFirst Degree Apprenticeship as part of the CyberFirst initiative to support undergraduates for a career in cyber security. In addition, the national centre has certified a number of degree programmes to signpost high quality degrees for those who are interested in pursuing a career in cyber security. NCSC has so far certificated 24 Master's degrees, three Integrated Master's degrees24Legend symbol denoting An Integrated Master's degree is a degree programme that combines undergraduate and postgraduate study into one. Students join the programme as undergraduates and study Bachelors level modules, before moving onto Masters level modules in the fourth or fifth year of the course. and five Bachelor's degrees in cyber security from 23 universities, as part of its programme to recognize high-quality courses.
Figure 1 - Formal educational activities to develop young talent
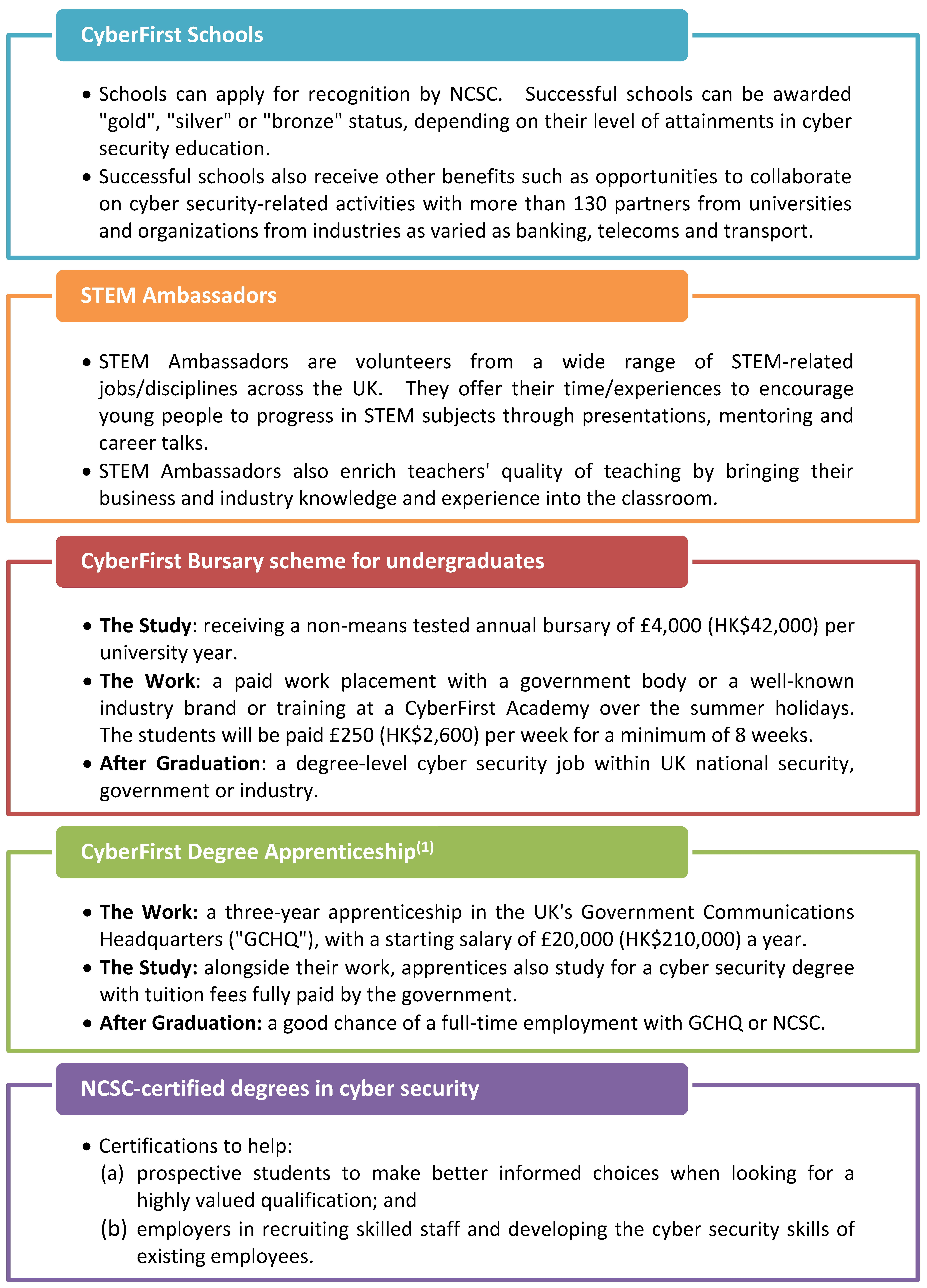
| Note: (1) | Applicants are required to achieve two "B" grades and one "C" grade in A-Levels in any subject and a grade of "5" in Mathematics in General Certificate of Secondary Education. |
| Source: Various government websites. | |
Qualifications and certifications
- In September 2019, DCMS commissioned the establishment of the UK Cyber Security Council through a consortium of cyber security professional bodies25Legend symbol denoting The Council is reportedly set to commence operations in April 2021. See (ISC)2 (2020b). The Council is to develop a professional framework for each of the various specialisms. Each framework sets out different career options and pathways, which includes clarification of the certifications and qualifications required at each occupational level26Legend symbol denoting This contrasts with Hong Kong's CCASP, which is a three-level certification scheme comprising the Practitioner, Registered and Certified Levels..
Extra-curricular activities
- NCSC has made use of extra-curricular activities to inspire young talent and develop their interests at a young age. It is particularly important for those who do not thrive in a formal education environment. As part of the National Cyber Security Strategy, CyberFirst features an array of extra-curricular activities aiming to help youths aged 11-18 explore the world of cyber security (Figure 2). It includes CyberFirst Girls' Competition, Cyber Discovery Programme and a series of short-term development courses.
Figure 2 - CyberFirst pathway for 11-18 years old
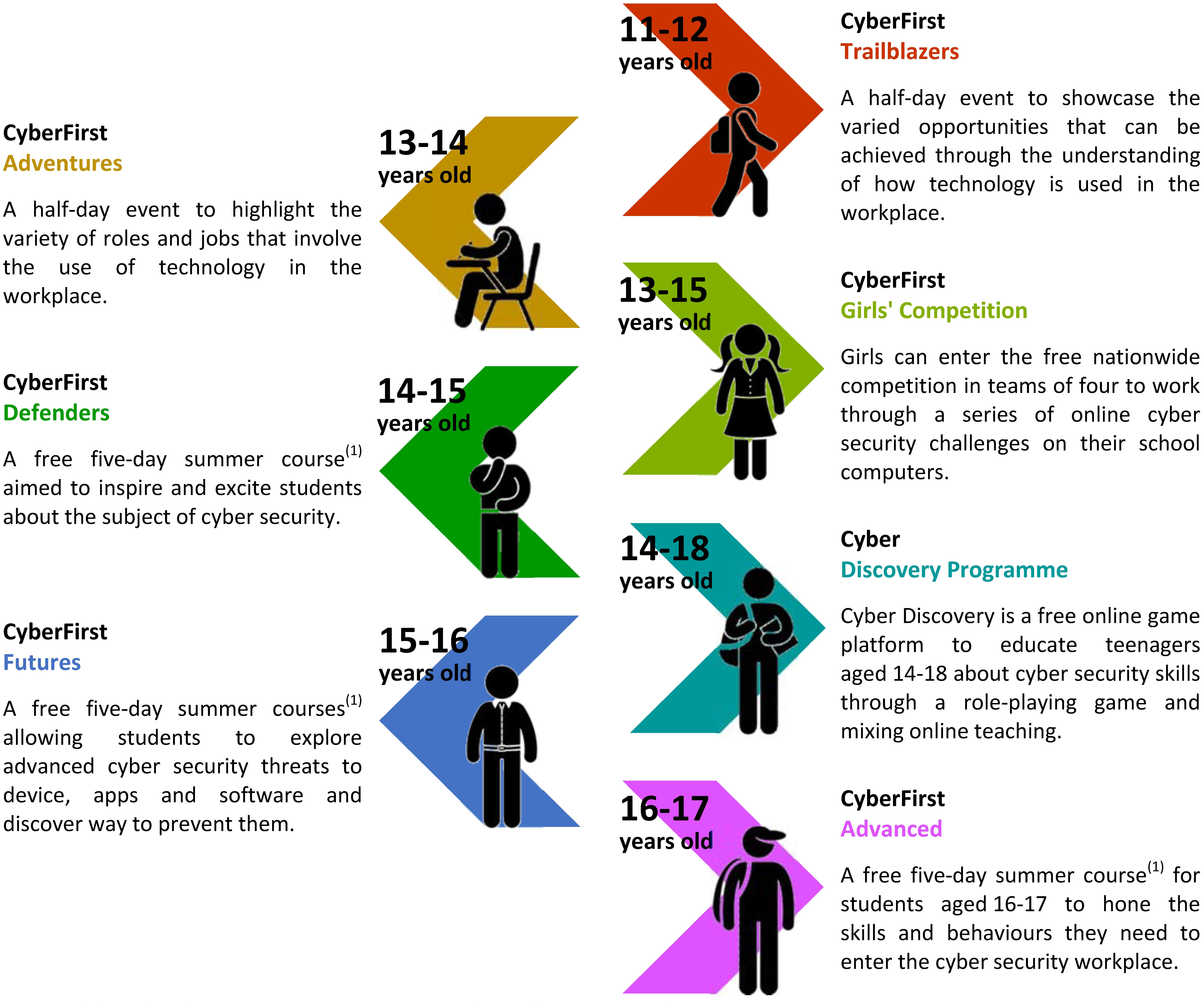
Source: CyberFirst (2020).
Retraining the current workforce
- Retraining and career transition has been considered by the UK government27Legend symbol denoting See Department for Digital, Culture, Media & Sport (2019). as a way to quickly boost the number and diversity of those entering the cyber security profession. One key intervention is the launch of the Cyber Skills Development Impact Fund28Legend symbol denoting The Fund was launched in May 2018 and expanded in October 2018. The third round of the Fund was launched in August 2019, whereby training providers can bid up to 50% of the total project costs, capped at £100,000 (HK$1.05 million), to jointly design programmes with employers for retraining people from diverse backgrounds. that provides funding and support to training providers and charities to develop and scale up effective retraining initiatives. These initiatives are delivered through various methods ranging from face-to-face teaching to online platforms, and hybrids of these two.
Concluding remarks
- The shortage of talent is one of the most critical issues the global cyber security profession is facing right now. The UK has advocated an ambitious multi-pronged approach to address the shortage, which features not only formal educational and extra-curricular activities, but also a specific retraining fund and a forthcoming certification scheme. These initiatives aim to encourage the professional development of those who are aspiring to work in cyber security to enter the profession, as well as helping those already in it to have their skills and expertise recognized more easily and in a clear and consistent way.
- The UK has achieved notable progress in developing the cyber security skills pipeline in recent years. These include (a) 12 000 girls taking part in the 2019 CyberFirst Girls' Competition; (b) over 55 000 young people having participated in Cyber Discovery and CyberFirst learning programmes as at June 2020; and (c) more than 900 students either on or recently graduated from the CyberFirst Bursary scheme during 2019-2020.
Prepared by Gary NG
Research Office
Information Services Division
Legislative Council Secretariat
22 January 2021
Endnotes:
References:
| 1. | Allianz Global Corporate & Specialty. (2020) Allianz Risk Barometer 2020.
|
| 2. | Census and Statistics Department. (2020a) Survey on Information Technology Usage and Penetration in the Business Sector for 2019.
|
| 3. | Census and Statistics Department. (2020b) Thematic Household Survey Report - Report No. 69 - Personal computer and Internet penetration.
|
| 4. | CyberFirst. (2020)
|
| 5. | Department for Digital, Culture, Media & Sport. (2018) Government Consultation: National Cyber Security Strategy - Developing the Cyber Security Profession in the UK Government.
|
| 6. | Department for Digital, Culture, Media & Sport. (2019) Initial National Cyber Security Skills Strategy: increasing the UK's cyber security capability - a call for views.
|
| 7. | GOV.UK. (2016) National Cyber Security Strategy (2016-2021).
|
| 8. | Hong Kong Computer Emergency Response Team Coordination Centre. (2020) Recent 10 Years of Security Incidents reported 2010-2020.
|
| 9. | Hong Kong Examinations and Assessment Authority. (2020) 2019 HKDSE Entry Statistics.
|
| 10. | House of Commons. (2020) Daily Report, 9 June.
|
| 11. | InfoCloud. (2020) Basics of Cloud Computing.
|
| 12. | Information and Innovation Bureau. (2020) Update on Information Security. LC Paper No. CB(1)306/19-20(05).
|
| 13. | InfoSec. (2020) Computer Related Crime.
|
| 14. | International Telecommunications Union. (2019) Global Cybersecurity Index 2018.
|
| 15. | (ISC)2. (2020a) Cybersecurity Workforce Study 2020.
|
| 16. | (ISC)2. (2020b) Help Shape the UK Cyber Security Council by becoming a Trustee.
|
| 17. | National Cyber Security Centre. (2020) Annual Highlight Report.
|
| 18. | National Cyber Security Centre. (various years) Annual Review.
|
| 19. | Vocational Training Council. (2018) Manpower Survey Report - Innovation and Technology Sector.
|
Essentials are compiled for Members and Committees of the Legislative Council. They are not legal or other professional advice and shall not be relied on as such. Essentials are subject to copyright owned by The Legislative Council Commission (The Commission). The Commission permits accurate reproduction of Essentials for non-commercial use in a manner not adversely affecting the Legislative Council. Please refer to the Disclaimer and Copyright Notice on the Legislative Council website at www.legco.gov.hk for details. The paper number of this issue of Essentials is ISE15/20-21.